Third-Party Risks Can Compromise You
Even if your systems haven’t been breached, a compromised vendor, partner, or external integration can put your organization at risk.
High-profile supply chain incidents show that attackers often exploit trusted third parties to access sensitive data or disrupt operations.
Teams relying on spreadsheets or periodic reviews lack real-time visibility, leaving blind spots that can turn into catastrophic breaches.

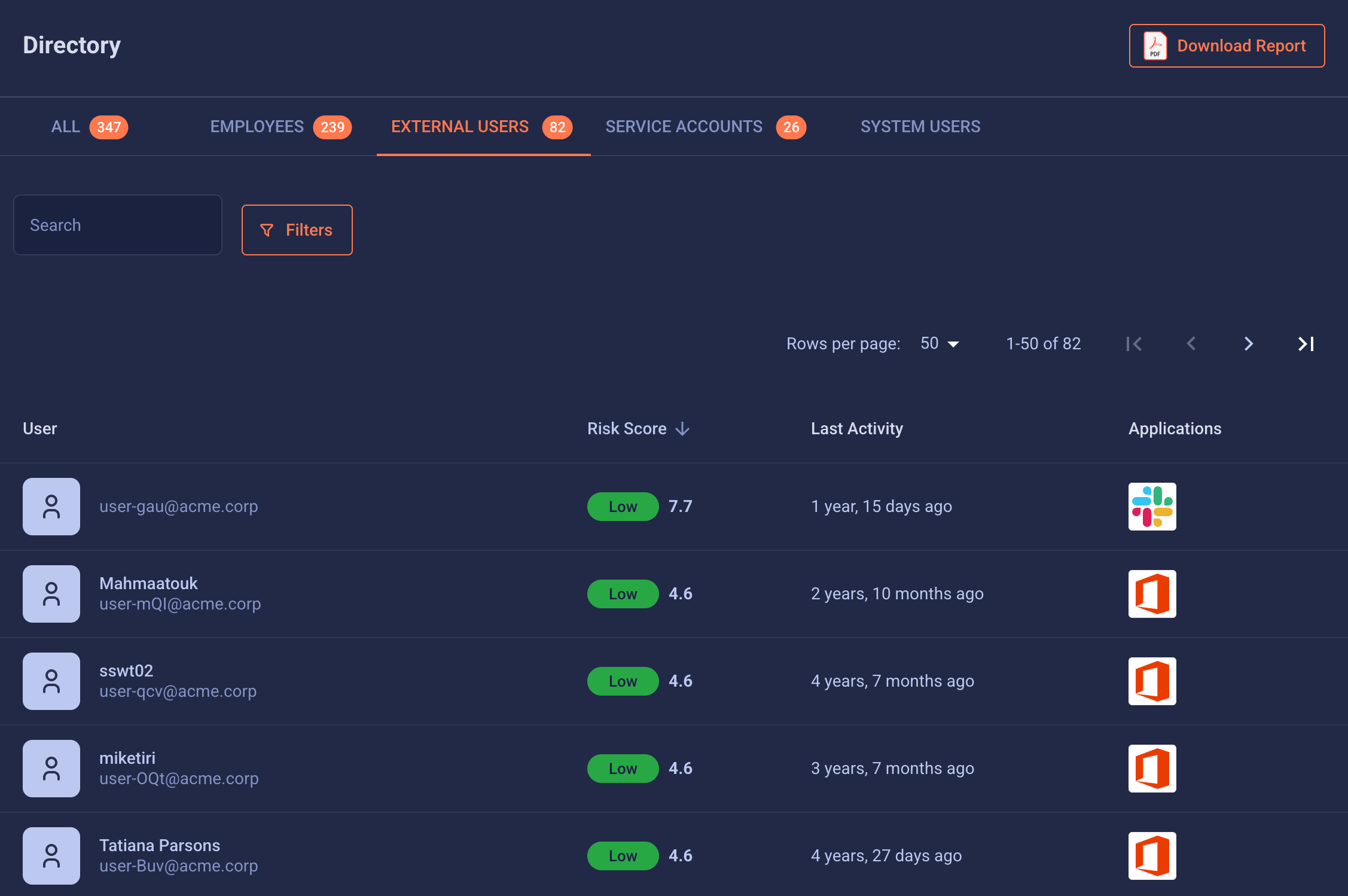

Every Weak Link Threatens Your Organization
CISOs and IT teams know the stakes: Your company can get breached even if you did everything right, but the vendor's account wasn’t secure. Lack of visibility increases the likelihood of:

Vendor breaches exposing your sensitive data or systems

Risky integrations bypassing your security controls
Unauthorized external access by partners or contractors

Operational disruption when compromised third parties affect business-critical workflows

Regulatory or contractual liability for failing to monitor and secure third-party access
Scenario
A vendor has access to several critical SaaS applications, but your team doesn’t know which accounts are active, who has MFA enabled, or whether any credentials have been exposed on the dark web.
One day, FrontierZero detects unusual behavior: a vendor account starts logging in from a device in a different city while accessing multiple apps simultaneously.
Traditional tools see each login in isolation and miss the risk.
FrontierZero connects the activity across identities and applications, alerting your team to take action before a potential breach impacts your organization.
FrontierZero Gives Full Supply Chain Visibility
Our identity-first platform provides real-time monitoring of every external connection, so your team can identify risks before they escalate. With FrontierZero, you get
- Continuous visibility of all vendors and external integrations across your SaaS environment
- Contextual risk insights highlighting which third-party connections pose the highest threat
- Automated alerts for suspicious or high-risk activity by external users
- Actionable recommendations to remediate risky access quickly
- Audit-ready reporting to demonstrate compliance and accountability




From Blind Spots to Full Control
FrontierZero transforms fragmented, outdated data into clear, actionable intelligence.
By continuously tracking third-party access and integrating identity and threat context, your team can secure the entire supply chain, reduce liability, and prioritize the highest risks with confidence.
See It in Action
Your organization should never be at the mercy of a vendor breach. Request a demo today and discover how FrontierZero helps you monitor, manage, and secure every vendor and integration in real time.
Ready to secure your SaaS?
No agents. No deployments. Just instant SaaS visibility.
The only SSPM platform built in the GCC, trusted globally for real-time SaaS visibility and security. Protecting organizations where traditional security ends.






