Hidden Tools Create Hidden Risks
Employees and teams often adopt unapproved SaaS applications or AI tools to get work done faster.
These shadow apps can store sensitive data, bypass IT controls, and create blind spots in your environment.
Most organizations only discover these tools after a security incident or compliance review, leaving teams exposed and reactive instead of proactive.


Every Unknown App Poses a Threat
CISOs and IT teams know that unmonitored tools can lead to:

Data leakage when unapproved apps store corporate information outside managed systems
Uncontrolled integrations that bypass security policies and expand attack surfaces
Compliance failures when shadow tools violate regulatory requirements

Operational disruption when critical workflows rely on unmanaged apps

Audit challenges from incomplete knowledge of what tools employees are actually using
Scenario
Marketing teams are using unapproved design tools, sales calls are joined by new AI notetakers, and HR relies on AI assistants for recruitment.
Your IT team doesn’t know where these tools store company data or which accounts they can access. One AI tool may have access to your corporate Google Drive while another shares data externally.
Traditional solutions monitor apps individually and miss the bigger picture.
FrontierZero connects activity across all unapproved tools, identities, and apps, giving your team visibility and control to protect company data before it’s exposed.
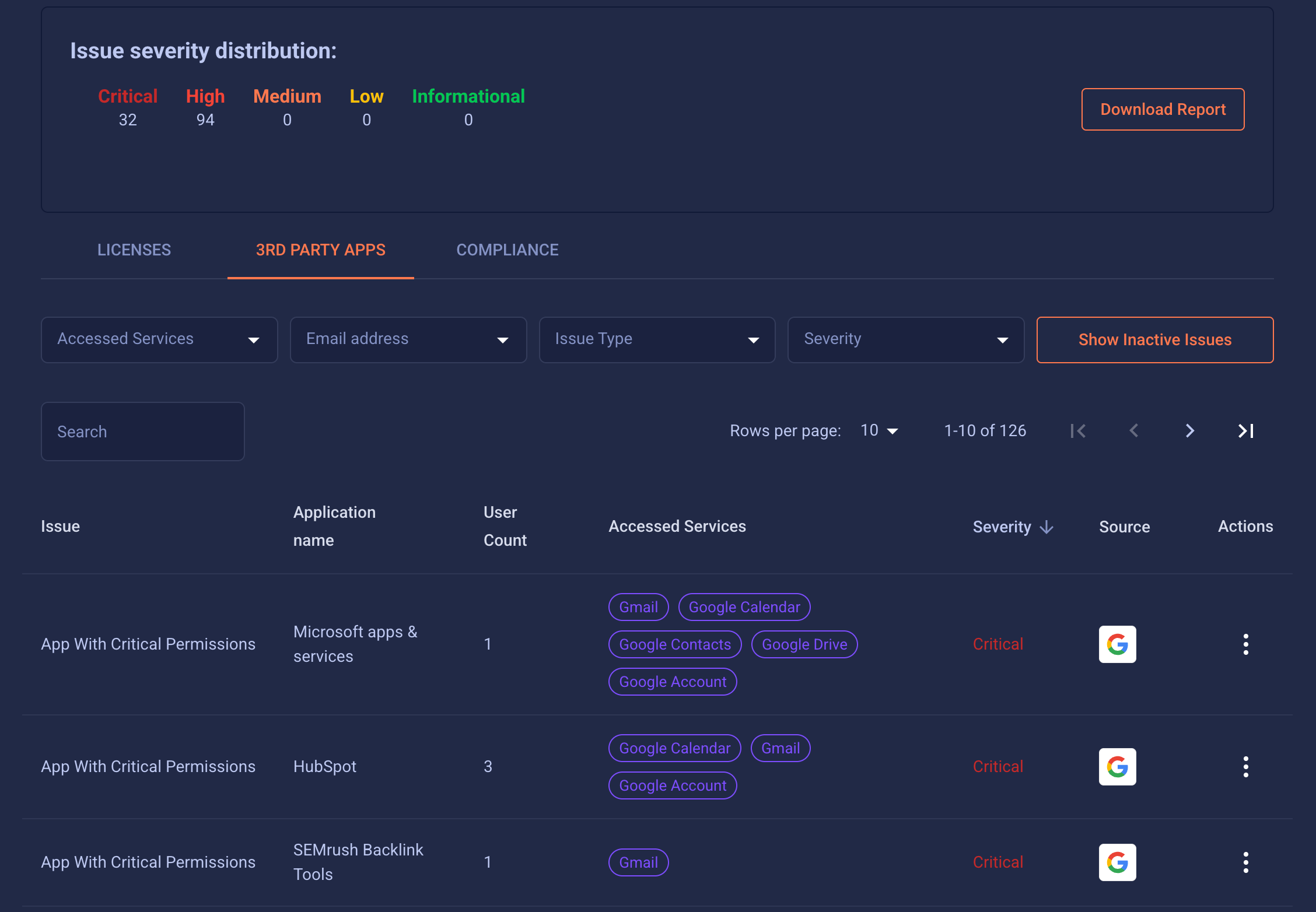
FrontierZero Reveals Every Unapproved Tool
Our identity-first platform provides complete visibility into shadow SaaS, shadow AI, unknown apps, and unapproved integrations. With FrontierZero, you get
- Continuous discovery of all applications in use, approved or not
- Contextual risk scoring to highlight tools that pose real threats
- Real-time alerts when new or suspicious applications appear
- Actionable remediation guidance so your team can bring risky apps under control
- Reporting and oversight to enforce governance and compliance confidently



From Blind Spots to Full Visibility
FrontierZero turns hidden, unmanaged tools into clear, actionable insight.
By correlating application usage with identity and behavior, your team can prioritize risk, prevent data exposure, and regain control over the SaaS environment.
See It in Action
Shadow SaaS and unapproved tools should never surprise you. Request a demo today and discover how FrontierZero helps your team identify, monitor, and secure every application in real time.
Ready to secure your SaaS?
No agents. No deployments. Just instant SaaS visibility.
The only SSPM platform built in the GCC, trusted globally for real-time SaaS visibility and security. Protecting organizations where traditional security ends.






