VPNs in Remote Work: Safeguarding Security Amidst Challenges of Throttling and Censorship

Table of Contents
Introduction
The rise of remote work has witnessed an exponential increase in the number of individuals working outside traditional office environments. With this shift, the need for secure online connections has become paramount.
Virtual Private Networks (VPNs) have emerged as a crucial tool for remote workers to ensure the privacy and security of their online activities. By encrypting internet traffic and establishing a secure tunnel, However, it is important to recognize that VPNs themselves are not infallible and come with their own set of security flaws and issues.
VPN throttling and censorship pose additional hurdles leading to decreased productivity and frustratingly slow internet speeds. Here’s how:
Definition
VPN Throttling refers to the intentional slowing down of internet speeds when using a VPN service, while censorship refers to the deliberate or systematic restriction, control, or interference with the use of VPNs.
Purpose
These techniques are often implemented by internet service providers (ISPs) to manage network congestion or to discourage VPN usage. Here are a few reasons behind such techniques:
-
Bandwidth management: ISPs may throttle VPN traffic to manage network congestion and allocate available bandwidth among different types of internet usage. By limiting the bandwidth for VPN connections, they can prioritize other types of traffic or ensure fair usage for all users.
-
Network optimization: In some cases, ISPs may throttle VPN traffic to optimize network performance or reduce latency. By controlling the flow of VPN data, they aim to ensure smoother and more efficient network operations.
-
Traffic shaping: ISPs may prioritize certain types of traffic, such as streaming services or online gaming, over VPN traffic. This prioritization can lead to slower VPN speeds or degraded performance, making VPN usage less desirable for certain activities.
-
National security concerns: Governments may perceive VPN usage as a potential security risk. Censorship measures can be implemented to mitigate this risk by preventing individuals from utilizing VPNs to facilitate illegal activities, such as cybercrime, or the dissemination of harmful content.
Impact on Remote Access and Performance
These practices primarily affect the speed and performance of internet connections when using a VPN. They can result in slower downloads, buffering during streaming, and delayed access to online resources. Here are some key impacts to consider:
-
Reduced productivity: Throttling VPN traffic can slow down access to company resources, leading to decreased productivity for corporate workers. Tasks that involve accessing large files, utilizing cloud-based applications, or collaborating remotely may be significantly affected by slower speeds, causing delays and inefficiencies.
-
Difficulty in remote work: Many corporate workers rely on VPN connections to access internal systems and resources while working remotely. Throttling can make it challenging to establish and maintain stable connections, impacting remote work capabilities and hindering communication and collaboration.
-
Impaired data transfers: Throttling can affect the speed and efficiency of data transfers for corporate workers. Uploading or downloading large files, syncing data, or conducting backups may become time-consuming and frustrating, potentially disrupting workflow and hindering critical business operations.
-
Impact on real-time applications: Throttling can impact real-time applications used by corporate workers, such as video conferencing or VoIP services. Slower speeds and increased latency can result in poor call quality, dropped connections, or difficulties in participating in virtual meetings or collaborative sessions.
Common Practices Used to Bypass VPN Throttling and Censorship
While individuals often resort to common practices to avoid VPN throttling and censorship, it’s important to acknowledge their limitations and potential drawbacks.
-
1. Switching VPN protocols: VPN protocols determine how data is encrypted, transmitted, and authenticated between a user’s device and the VPN server.
-
2. Utilizing obfuscated servers: Obfuscated servers are specifically designed to disguise VPN traffic and make it difficult to detect or block.
-
3. Employing stealth techniques: These techniques aim to make VPN traffic appear as regular internet traffic, thereby evading detection and blocking measures.
Despite these efforts, ISPs can still identify and disrupt VPN traffic, impacting the effectiveness of these methods.
Additionally, relying on dedicated IP addresses or constantly changing server locations can be inconvenient and may not always provide the desired outcome. These common practices require technical knowledge, can be time-consuming, and may not offer a consistent solution for everyone.
Legal Considerations
It’s crucial to stay informed about the legal and regulatory environment regarding VPN usage in your jurisdiction. While bypassing VPN restrictions may help access blocked content, it’s important to ensure that your actions comply with applicable laws and regulations.
VPN Alternatives for Your Remote Workforce
Finding alternatives for VPN connections when your ISP is throttling the VPN connection is crucial to ensure smooth and secure remote work for your employees. Here are some alternatives to consider:
-
Agentless Zero Trust Network Access (ZTNA): ZTNA is an emerging secure access model that focuses on identity verification and granular access control. Instead of relying on a traditional VPN, ZTNA solutions authenticate users and devices before granting access to specific applications or resources. The agentless approach eliminates the need to install dedicated software agents on endpoints while still providing robust security.
-
Cloud-based Virtual Desktop Infrastructure (VDI): Cloud-based VDI solutions allow employees to access a virtual desktop environment hosted in the cloud. With VDI, employees can securely access their work desktop, files, and applications from any device with an internet connection. By leveraging the cloud infrastructure, VDI eliminates the need for a VPN connection and can provide consistent performance even with VPN throttling.
-
Secure File Sync and Sharing Services: Instead of relying on VPNs for file access, you can consider using secure file sync and sharing services like Dropbox, Google Drive, or Microsoft OneDrive. These services provide secure cloud storage, file synchronization, and collaboration features, allowing employees to access and share files without the need for a VPN connection.
-
SD-WAN Solutions: Software-defined Wide Area Network (SD-WAN) technology enables secure and optimized connectivity between remote locations and the corporate network. SD-WAN solutions can utilize multiple internet connections, including 4G/LTE, MPLS, or broadband, to establish secure and reliable connections for remote employees.
When considering alternatives to VPN, it’s important to evaluate each solution’s security, performance, ease of use, and compatibility with your existing infrastructure. It’s also crucial to assess the regulatory and compliance requirements specific to your industry and ensure that the chosen alternative meets those requirements.
Talk to us to get a free consultation.
How We Can Help
We at FrontierZero are offering an innovative solution to effectively overcome the challenges posed by VPN throttling and censorship. Our approach involves providing an agentless cloud-based platform that ensures a smoother and more productive remote work experience while prioritizing security.
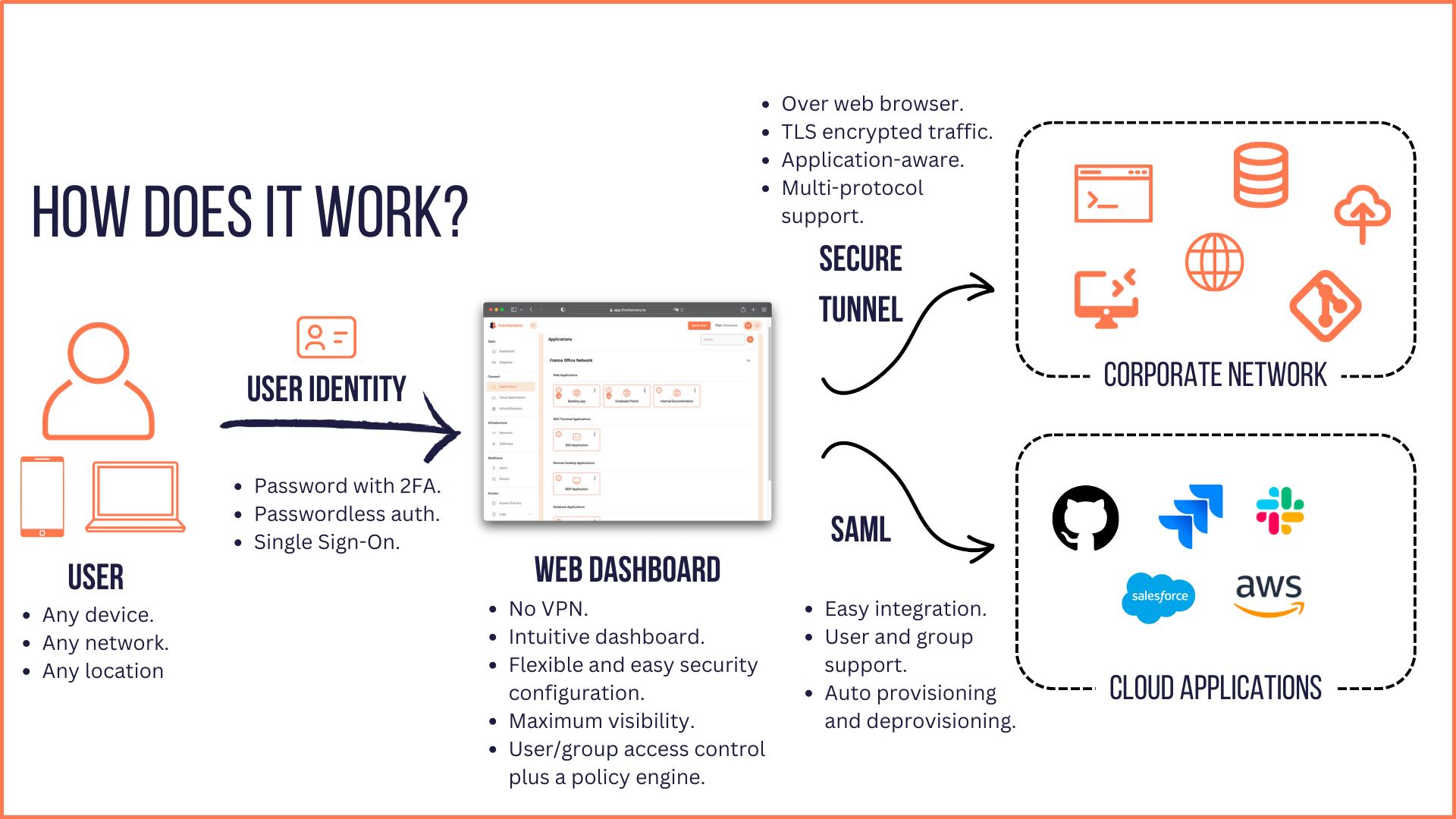
By adopting an agentless approach, our platform eliminates the need for installing additional software or applications on users’ devices. This simplifies the setup process and reduces potential compatibility issues, enabling seamless integration with existing systems and unhindered access to corporate applications.
Furthermore, we always prioritize security, offering peace of mind to remote workers and organizations, knowing that their information is safeguarded throughout the online work process.
To know more, you can request a free trial or contact us directly at [email protected].

 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter