The Importance of Monitoring Multi-Factor Authentication in Your Organization

Table of Contents
Introduction
Multi-factor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction.
Types of Multi-factor Authentication Methods
There are three main methods people use as means of Multi-factor authentication. These include:
- Something You Know:
- Password: A secret word or phrase known only to the user.
- PIN: A personal identification number.
- Security Questions: Answers to personal questions.
- Something You Have:
- Smartphone: A device used to receive authentication codes via SMS, email, or an authenticator app.
- Hardware Token: A physical device that generates a time-based or one-time password.
- Smart Card: A card with embedded integrated circuits for authentication.
- Something You Are:
- Biometrics: Fingerprint, facial recognition, iris scan, voice recognition.
- Behavioral Biometrics: Typing patterns, gait, or other unique behaviors.
Why Multi-Factor Authentication Matters
Implementing MFA significantly reduces the risk of stolen credentials, as it adds an extra layer of security beyond just a username and password. According to recent studies, MFA can block over 99.9% of account compromise attacks.
For executives overseeing an organization’s security, enforcing MFA is not just a best practice—it’s an essential safeguard. It ensures that even if credentials are stolen through phishing, malware, or other means, unauthorized access is thwarted, protecting sensitive data and maintaining the integrity of your systems.
The Snowflake Incident: A Wake-Up Call
A recent incident involving Snowflake, a popular data warehousing service, underscores the necessity of stringent MFA policies. Hackers successfully stole customer credentials through malware, gaining access to Snowflake systems. Once inside, they downloaded vast amounts of data, using it to extort the affected customers. While Snowflake wasn’t entirely at fault, this breach highlighted a significant vulnerability: the absence of enforced two-factor authentication.
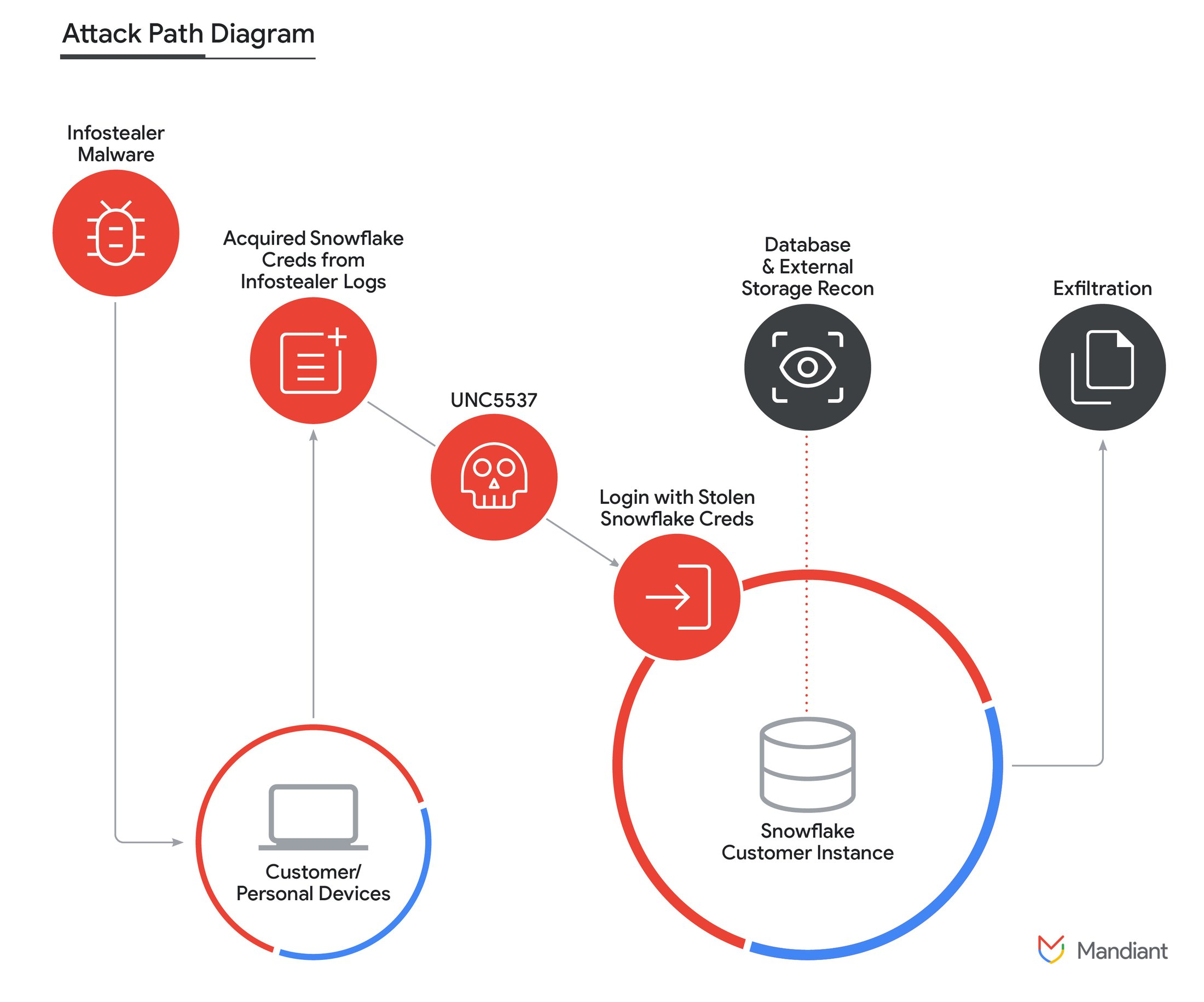
In response, Snowflake has rolled out an option to enforce MFA, allowing administrators to add an essential layer of security.
However, this incident begs a crucial question: What other applications within your organization are you overlooking in terms of MFA enforcement?
The Blind Spots in Your SaaS Ecosystem
Executives often assume that high-profile incidents like the Snowflake breach are isolated events. Yet, this assumption can lead to a false sense of security. Many SaaS applications and cloud infrastructures may not have robust MFA policies in place, leaving your organization exposed to similar threats.
Key Points to Consider
- Comprehensive Audits: Regularly audit all SaaS applications and cloud services used within your organization. Ensure that MFA is enforced across the board, not just in your most critical systems.
- Automated Monitoring: Implement tools that automate the detection of MFA enforcement gaps. This reduces the manual workload on your IT team and ensures continuous protection.
- User Education: Educate your users about the importance of MFA and encourage them to adopt best practices. A well-informed workforce is your first line of defense against cyber threats.
- Policy Enforcement: Make MFA a mandatory policy for all users accessing sensitive data and systems. Ensure that your administrators have the tools to enforce these policies effectively.
How FrontierZero Can Help
At FrontierZero, we understand the complexities and challenges of managing a diverse SaaS ecosystem. Our platform provides a single pane of glass visibility over your SaaS applications, allowing you to see which applications are enforcing MFA and which are not. With our automated detection capabilities, we help you identify and remediate gaps in MFA enforcement, ensuring that your organization remains secure against potential breaches.
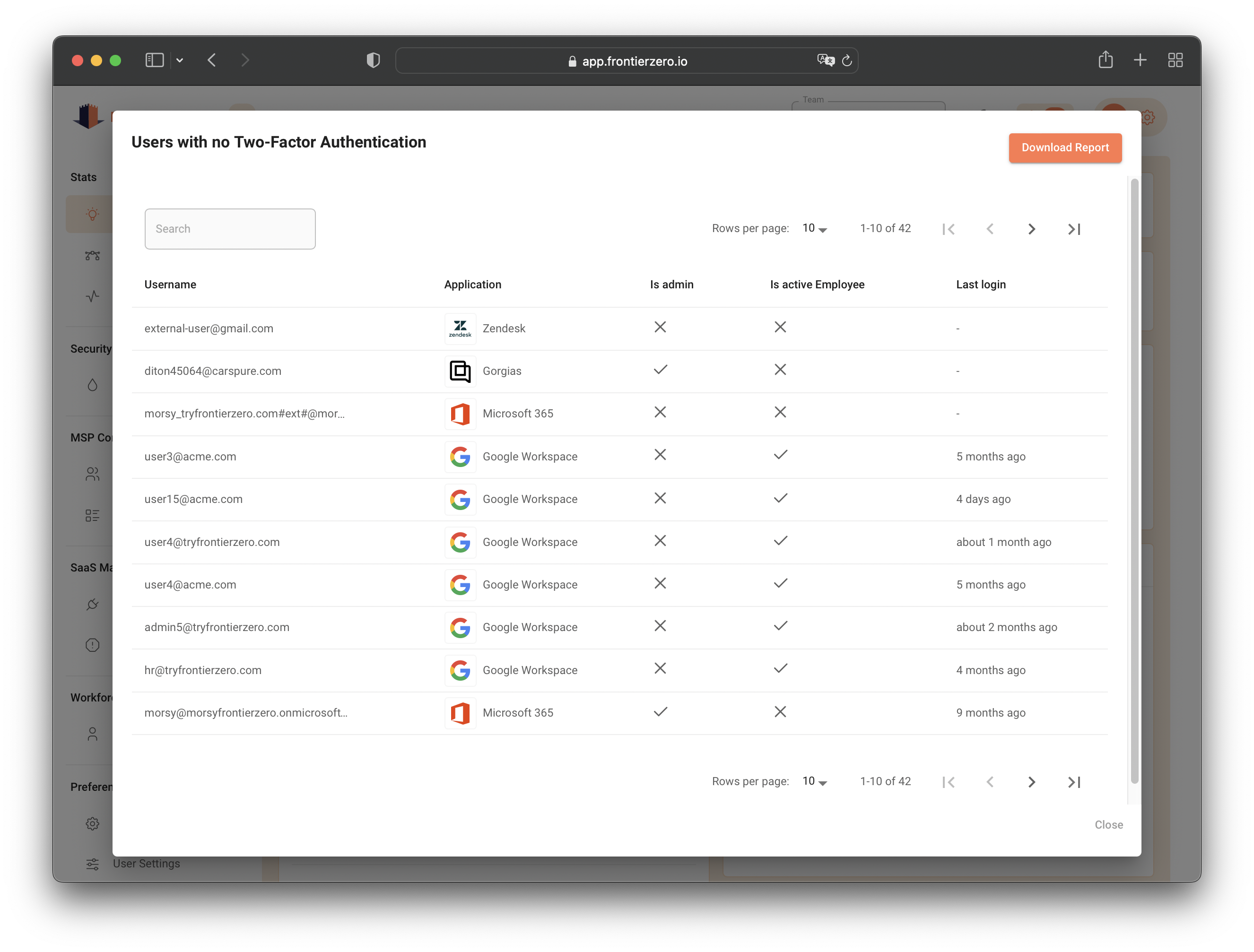
Don’t wait for the next incident to highlight vulnerabilities in your security posture. Prioritize your MFA enforcement by leveraging the right tools.
Want to know more? You can request a free trial or contact us directly at [email protected] to know more!

 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter