Are Shadow Apps Stealing Your Business Data?

Table of Contents
Introduction
The question of data security isn’t just for IT departments—it’s a boardroom concern. With the proliferation of SaaS applications and cloud infrastructure, ensuring the safety and privacy of business data is more crucial than ever. CEOs must be aware of where their company’s data is, who has access to it, and how it’s being used.
The rise of AI tools and their integration into everyday business operations have added a new layer of complexity, often leading to the unrestricted access of sensitive data.
Importance of Knowing Where Your Data Is
Data is the lifeblood of modern enterprises. It drives decision-making, fosters innovation, and fuels growth. However, with great power comes great responsibility. Protecting business data isn’t just about avoiding financial losses or legal repercussions—it’s about maintaining the trust of customers, partners, and stakeholders.
Data breaches and cyber-attacks are becoming increasingly common, and therefore, CEOs need to have a clear understanding of their data landscape.
Risks of Shadow SaaS Applications
Shadow SaaS applications are those unauthorized applications that employees use without formal approval from the IT department. These applications can easily bypass traditional Data Loss Prevention (DLP) products because they operate outside the visibility and control of IT security protocols. Here’s how they do it:
- Unmonitored Channels: Shadow SaaS applications often access data through OAuth, which can be outside the scope of traditional DLP monitoring. DLP systems typically focus on known channels and authorized applications, leaving a blind spot for unauthorized tools.
- Encryption Challenges: Many shadow SaaS applications use strong encryption, making it difficult for DLP products to inspect and control data flows effectively. This encryption can obscure the data transfer activities from DLP scrutiny.
- Data Fragmentation: Shadow SaaS applications can fragment data across multiple platforms, complicating the task for DLP systems to track and manage data movement comprehensively.
- User Behavior: Employees might inadvertently or deliberately use shadow SaaS applications to circumvent security policies, believing that these tools make their work easier. This behavior often goes undetected by DLP systems focused on monitoring sanctioned applications.
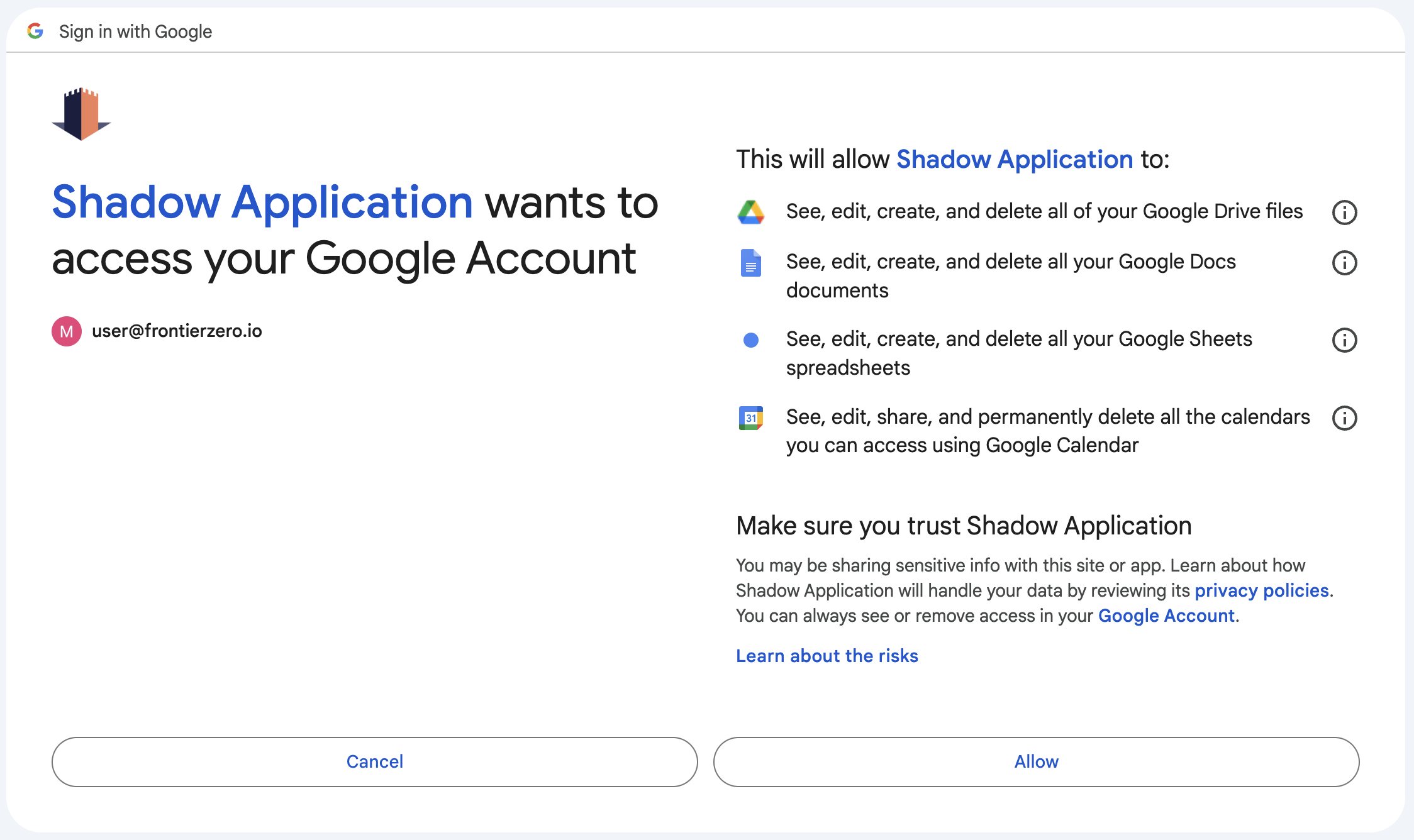
The Rise of AI Tools
AI tools have become indispensable in today’s business environment, offering benefits like improved efficiency, enhanced decision-making, and predictive analytics. These tools range from virtual assistants and chatbots to sophisticated data analytics platforms.
However, the convenience they offer often comes with hidden risks. AI tools typically require extensive access to data to function effectively, which can lead to potential security vulnerabilities if not properly managed.
Types of Data Requested by AI Assistants
AI assistants and tools request various types of data to perform their tasks, including:
- Email Access: AI tools that manage schedules, set reminders, or provide email summaries often require access to an employee’s email account. This access can include reading, modifying, and sending emails on behalf of the user.
- Document Access: Tools that assist with document management or content creation may request access to cloud storage services like Google Drive or Microsoft OneDrive, gaining the ability to read, write, and share documents.
- Calendar Access: AI scheduling assistants often need access to calendar data to schedule meetings, send invites, and provide reminders. This access can include viewing all calendar entries and sometimes even modifying them.
- CRM Data: AI tools that enhance customer relationship management may need access to CRM systems to analyze customer interactions, predict sales trends, or provide personalized customer service recommendations.
- Financial Data: AI-powered financial tools might request access to accounting software to offer budgeting advice, detect anomalies, or forecast financial trends.
- Conversations and Meetings: some tools might request permission to join meetings, listen to them and take notes to summarize them later on.
Impact of Unrestricted Data Access
- Data Privacy Concerns: Unrestricted access to sensitive data by AI tools can lead to privacy breaches if the data is mishandled or accessed by unauthorized parties.
- Data Leakage: Improperly secured AI tools can become entry points for hackers, leading to data leaks that can have severe financial and reputational consequences.
- Compliance Issues: Allowing AI tools unrestricted access to data without proper oversight can result in non-compliance with data protection regulations like GDPR, CCPA, and others, leading to legal and financial penalties.
- Intellectual Property Risks: AI tools with access to proprietary business data can inadvertently expose intellectual property, giving competitors an unfair advantage.
How to Remain Vigilant
- Educate Employees: Regular training sessions on data security and the risks associated with third-party applications can help employees make informed decisions.
- Implement Access Controls: Ensure that only authorized applications have access to sensitive data. Regularly review and update access permissions.
- Monitor and Audit: Continuously monitor the applications that have access to your data. Conduct regular audits to identify and mitigate potential risks.
- Leverage Security Tools: Utilize advanced security tools that detect and remediate shadow SaaS applications—those unauthorized applications that operate under the radar.
Protecting Your Business with FrontierZero
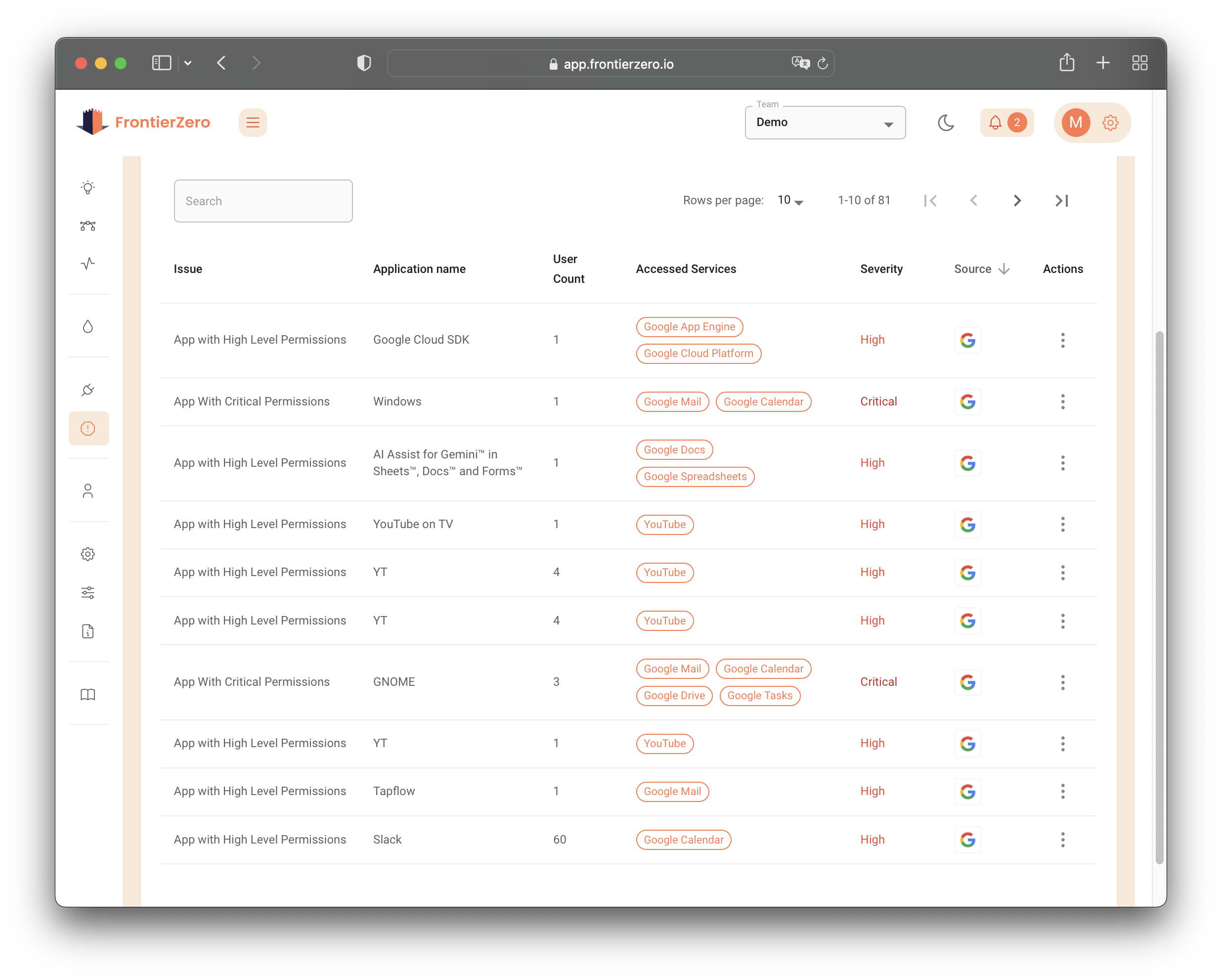
At FrontierZero, we understand the complexities of modern data security. Our platform integrates with various SaaS applications to provide a comprehensive view of all OAuth applications accessing your company’s data.
We specialize in detecting and remediating shadow SaaS applications, ensuring that your business data remains secure. Don’t leave your data’s safety to chance—let FrontierZero be your vigilant guardian.
Want to know more? You can request a free trial or contact us directly at [email protected] to know more!

 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter